On-Chain Goldmine
Insider’s Guide to MEV
tl;dr
MEV refers to the additional value miners or validators extract from block production, beyond standard block rewards and transaction fees. It arises from the manipulation of transaction order in the mempool for profit, a practice that became prominent with the advent of Ethereum and DeFi. MEV exploits include front-running, back-running, and other strategies that leverage predictable outcomes of complex transactions.
The MEV supply chain involves users, wallets, searchers, builders, and validators, each playing a specific role in the blockchain ecosystem. Issues like predatory practices, user impact, and security threats emerge due to the mismatched ordering between block sequencing (governed by consensus mechanisms) and transaction ordering (influenced by fee auctions).
Solutions like Proposer-Builder Separation (PBS), Protocol-Enforced Proposer Commitments (PEPC), Single Unifying Auction for Value Expression (SUAVE), and mev-boost address these challenges.
PBS and PEPC aim to decentralize block creation and enforce proposer commitments.
SUAVE provides a decentralized platform for transaction sequencing, and
mev-boost, an implementation of PBS, enables fair exchange between proposers and builders.
Collectively, these techniques strive to mitigate the negative impacts of MEV, ensuring fairness and efficiency in the blockchain environment. However, the above list is not exhaustive.
Introduction
MEV refers to the maximum value that can be extracted from block production beyond the standard block rewards and transaction fees typically collected by miners or block producers. It involves these nodes analyzing pending transactions in the mempool and selectively including, excluding, or reordering them within a block to generate additional profits. By reorganizing transactions in this manner before they are finalized on-chain, the block producers or other network participants are able to capitalize on certain transaction orderings.
How did MEV come to be?
The concept of MEV originated particularly with the rise of Ethereum and DeFi. With any blockchain system, transactions are grouped into blocks, which are then added to the blockchain. Miners (in proof-of-work systems like Bitcoin and Ethereum 1.0) or validators (in Proof-of-Stake systems) are responsible for this process. They typically select transactions based on transaction fees, adding the most lucrative ones to the next block. A defining feature of blockchains is the transparency and predictability of transactions. Before being confirmed, transactions sit in a public pool known as the mempool. This visibility allows anyone to view and analyze unconfirmed transactions.
Ethereum, with its smart contract capabilities, ushered in a new era of complex transactions. This complexity went beyond simple transfers of value (like in Bitcoin) and included sophisticated interactions with DApps, particularly in DeFi. With DeFi, numerous financial activities like trading, lending, and borrowing became possible directly on the blockchain. This led to the creation of various complex financial instruments and interactions, often tied to Ethereum's smart contract functionality.
The complex interactions with smart contracts in Ethereum's DeFi ecosystem made certain transaction outcomes predictable. For instance, a large trade on a decentralized exchange could predictably affect the price of an asset. Observant validators and traders realized that by studying the mempool, they could predict the outcomes of certain transactions and, importantly, act on this knowledge. This included strategies like
front-running (executing a transaction before a known upcoming transaction) and
back-running (executing a transaction immediately after a known transaction).
The term "Miner Extractable Value" (MEV) was first formalized in a paper titled "Flash Boys 2.0" by Phil Daian and others in 2019. The paper highlighted how miners could exploit their position to extract additional value from transaction ordering.
Initially, the focus was on miners in a Proof of Work system (hence "Miner" Extractable Value). However, with Ethereum's transition to Proof of Stake and similar mechanisms being relevant in other blockchains, the term evolved to "Maximum" Extractable Value, encompassing a broader range of actors, not just miners. MEV has since broadened to include various forms of value extraction by validators, bots, and traders, not just miners. This includes not only front-running and back-running but also complex strategies like sandwich attacks, liquidations, and arbitrage across different DeFi platforms.
MEV Supply Chain
Each plays a distinct role in the transaction and block creation process on blockchain networks like Ethereum.
User:
Role: The user initiates the process by having an intention to make a state transition on the blockchain. This could be any action that alters the blockchain's state, like a token swap or contract interaction.
Example: A user wanting to swap USDC for ETH at the best possible rate.
Limitation: Since users cannot directly interact with the blockchain, they require tools to execute their intentions.
Wallet (Application Layer):
Role: The wallet acts as the user interface, helping encode the user's intent into a transaction that the blockchain can process. This includes not just the wallet interface but also dApp UIs and smart contract protocols.
Responsibility: Developers at this layer decide how to handle MEV. They can route user transactions to public pools, where they're exposed to all searchers, or to private systems like Flashbots Protect, which offers more restricted access.
Searcher:
Role: Searchers aim to extract as much MEV as possible for themselves. They collect user transactions from various sources and convert them into complex transaction types, like bundles.
Importance: They play a crucial role in providing liquidity, arbitrage, and liquidations, which are essential for market functionality.
Challenge: In a dysfunctional system, searchers might extract disproportionate value compared to the services they provide.
Builder (e.g., Mining Pools, Sequencers):
Role: Builders aggregate transactions from different sources to construct a block. In Ethereum, mining pools currently perform this role, and in Layer 2 (L2) systems, the sequencer acts as the builder.
Function: They assemble transactions into a block or rollup payload for submission to the main chain (Layer 1).
Validator:
Role: Validators are responsible for consensus duties, which include validating and finalizing blocks.
Evolution: Historically, builders and validators were the same entity. However, initiatives like the Block Proposer/Builder Separation (PBS) aim to separate these roles.
Goal: According to Vitalik Buterin's "Endgame" post, this separation seeks to maximize validator decentralization and enhance security and efficiency in the system.
Each of these roles contributes to the overall functioning of the MEV supply chain, ensuring that transactions are initiated, processed, and validated in a decentralized blockchain environment. The system aims to balance efficiency, security, and fair value extraction, though it faces challenges like potential disproportionate value extraction by searchers and the need for further decentralization in the builder and validator roles.
Key Concepts
MEV involves a series of interconnected key concepts that define how value can be extracted from transaction ordering. Understanding each of these concepts in detail provides a clearer view of the MEV landscape.
1. Pending Transactions and the Mempool
Mempool Basics: In a blockchain network, when users initiate transactions, these do not get added to the blockchain immediately. Instead, they enter a waiting area known as the mempool (short for memory pool). This pool is a collection of all the transactions that have been broadcast to the network but not yet included in a block.
Mempool Visibility: Transactions in the mempool are visible to everyone in the network. This transparency allows participants to see and analyze these pending transactions, which is a fundamental aspect of how MEV is identified and executed.
2. Role of "Searchers" in MEV
Identifying Opportunities: "Searchers" are individuals or entities who scan the mempool for profitable opportunities. They analyze pending transactions to identify patterns or situations that can be exploited for financial gain.
Strategies of Searchers: These strategies might include identifying large trades that will impact the market price of an asset, finding undercollateralized loans ripe for liquidation, or spotting opportunities for arbitrage.
3. Automated MEV Bots
Function of MEV Bots: Searchers use automated bots to execute MEV strategies. These bots are programmed to act rapidly upon identified opportunities in the mempool. Due to the competitive nature of MEV, speed is crucial, as multiple parties might be trying to exploit the same opportunity.
Transaction Submission: MEV bots are capable of quickly generating and submitting transactions to the blockchain network. They are designed to optimize for factors like gas price to ensure their transactions get included in a block promptly and in the desired order.
4. Common MEV Techniques
Arbitrage Between DEXs: This involves exploiting price differences for the same asset across different decentralized exchanges (DEXs). Bots can simultaneously buy an asset at a lower price on one DEX and sell it at a higher price on another.
Sandwich Attacks: This tactic involves placing two transactions around a large trade – one before and one after – to profit from the price movement caused by the large trade.
Liquidations: In DeFi, if a loan becomes undercollateralized, it can be liquidated. Bots monitor for such situations and quickly execute liquidations for profit.
Just-In-Time (JIT) Liquidity: This involves adding liquidity to a pool just before a large transaction and then removing it immediately afterward, allowing the liquidity provider to earn a significant portion of the trading fees from that transaction.
5. Reordering Transactions for MEV
Importance of Transaction Order: The ability to reorder transactions within a block is crucial for MEV. By manipulating the order of transactions, searchers can maximize their profits from the opportunities identified.
Impact on Network: This reordering can affect the network's operation, as it might lead to prioritization of MEV transactions over regular user transactions, potentially increasing transaction fees and affecting network throughput.
6. Incentivizing Miners/Builders
Role of Miners/Builders: Miners (in Proof of Work systems) or builders (in some Proof of Stake systems) are responsible for assembling blocks. They have the power to decide which transactions are included in a block and in what order.
Fee Incentives: Miners/builders are incentivized to include MEV transactions in a block in the desired order through fees. This might include higher transaction fees offered by searchers or direct payments through systems like Flashbots, which provide a marketplace for MEV transactions.
Why Does MEV Exist
MEV profits generally emerge from two areas:
Rearranging or front-running transactions to profit from price movements caused due to the execution of certain trades i.e, buying an asset fractionally before a large order likely to pump the price.
Censoring/blocking disadvantageous transactions or manipulating ordering for users to trigger penalties or liquidations from which miners extract the seized value or collateral assets.
Prominent examples of MEV extraction strategies include things like:
Sandwich attacks before large DEX trades to profit from likely slippage
Liquidations from forced adverse orderings
Priority gas auctions from users bidding to boost transaction positions
Automated revenue from NFT price arbitrages
Manipulating prediction market resolutions
Why Opportunity Exists – Separation of Ordering
The core reason MEV opportunities exist is because two largely distinct mechanisms currently facilitate ordering within cryptocurrency systems –
one handling inter-block sequencing based on Proof of Work/Stake selection of validated chains, and
another handling intra-block ordering of transactions based predominantly on gas auctions where users bid for priority placement.
Block Ordering – This refers to the consensus layer mechanisms for determining the canonical sequence of accepted blocks. This involves computational races in PoW chains for noisy block production or locked staking capital for PoS rulesets. The common goal is that peer choice of the valid chain follows objective rules around the longest chains, approving hashes, bonded assets, etc., to make sustained attacks prohibitively expensive.
Transaction Ordering – For arranging transactions within mined blocks however, largely separate principles are used. While base fees offer compensation for security costs, the prioritization across queued transactions uses market mechanisms. Users subjectively bid gas fees aiming to outrank peers and boost order priority for rapid execution.
This gas fee auction allows miners to optimize profit but presents two issues:
It makes the specific transaction arrangement within new blocks easily manipulable based on bid incentives rather than relying on a statistically randomized hash output ordering say.
The incentives around transaction ordering risk misaligning with honest participation in the blockchain’s consensus rules and procedures for choosing valid chains.
Essentially, the transaction layer ordering diverges from the degree of verification and tamper-resistance offered at the block consensus layer. This allows miners to game the system and extract additional profits without undermining security since their choices only affect intra-block arrangements rather than the blockchain validity rules.
But while network security remains intact, it introduces adverse effects seen from MEV extraction techniques, which didn’t appear in earlier transaction-fee-based systems since miners previously couldn’t isolate and optimize ordering for profit.
Issues Introduced by Unchecked MEV Practices
The extraction of MEV by miners/validators/other actors doesn’t clearly violate the consensus layer security guarantees around blocks since manipulation is isolated to changes in transaction positions. But several problems manifest from unchecked mining behaviors, including:
Predatory Revenue Practices – Miners directly profit from things like front-running user transactions to capitalize on likely price impacts or deliberately arranging transactions to trigger penalty positions at user expense. This represents a highly adversarial stance rather than collaborative security.
User Impacts – Frontal running слвесонз or forced slippage from transaction reordering presents costs and unfair outcomes to ordinary users from miners gaming the system. Predictable pricing or execution is lost.
Reduction of Security Incentives – Since MEV profits can significantly outweigh regular fees, miners risk ignoring or not extending chain progression to keep mining a side chain they can manipulate if extraction revenues exceed consensus rewards. This threatens availability and liveness.
Centralization Pressures – Computationally intensive strategies coupled with favorable network positioning makes extracting MEV at scale accessible largely to a few dominant mining pools rather than smaller players. This concentrates ordering powers.
Collusion Opportunities – Coordinated transaction censorship or reordering alliances could emerge among miners if left unchecked, posing even bigger threats to ecosystem fairness and user protections.
In essence, left unmanaged – MEV continues scaling extraction economies to destabilizing proportions by compromising incentives around security and progression by deemphasizing consensus rewards over pursuing manipulation profits among miners. Users suffer due to unchecked extraction behaviors as well.
Key Difference From Typical Fee-Based Systems
Earlier cryptocurrency transaction fee models were still optimized for miner/validator profits but didn’t enable the additional gaming strategies miners now utilize around the extraction of MEV. Some key differences include:
Before MEV dynamics emerged, miner extractable value was largely limited to the standard fees users chose to prioritize their transactions. The bidding process determined pricing but didn’t allow arbitrary ordering manipulation.
Base network security was covered via block rewards, so fees predominantly offered synchronized benefits – rapid confirmations for users and sustainable miner compensation.
Zero-sum gaming behaviors were largely absent since miner interests couldn’t be isolated from user interests in terms of execution certainty and sequence integrity. All participants shared universal ordering goals.
However, in PoS, the emergence of Turing complete computation and smart contract-based ecosystems introduced state manipulation vulnerabilities not present in simpler UTXO chains. This expanded the attack surface for miners, especially as activities grew more complex. Creative strategies emerged among miners to chart transaction dependencies to capitalize on likely execution flows. Order manipulation showed prospects for exponential returns exceeding standard block provisions.
We explored Ethereum’s fee markets (EIP-1559, EIP-4844) and the detailed concept of order flows previously in our research, in case you need a primer for better understanding.
As MEV practices formalized, miner goals could differ radically from those of ordinary users who now faced adverse selection, discrimination, and even predation from parties deciding inclusion and arrangements.
This misalignment stems fundamentally from the disconnected ordering systems – one securing overall blockchain history and the other governing component transactions. With the two models differing in aspects like tamper resistance and manipulation potential, incentives suffer.
The Root Cause of Mismatched Ordering
Analyzing the landscape, the root reason MEV practices and resultant toxicity emerge is that transaction order is governed by a separate mechanism from the consensus system ordering blocks.
There exists little correlation between the priority calculations determining block sequencing versus those deciding transaction positions within new blocks.
This allows contradictory incentives and opportunities for one ordering market to be played against another.
The distinct systems emerge from partial decentralization rather than unifying both layers wholly under the umbrella of Nakamoto consensus, for instance. While block production adheres to agreed computational rules, internal contents get ordered through fee auctions, creating mismatched trust and tamper-resistance guarantees.
In blockchains, there are fundamentally two layers of operation concerning the creation of a blockchain ledger.
The first is the block level, where blocks are created and added to the blockchain.
The second is the transaction level, where individual transactions are ordered and included within these blocks.
Block sequencing is governed by the blockchain's consensus mechanism, such as Proof of Work (PoW) or Proof of Stake (PoS). This mechanism determines which block gets added to the blockchain next, based on certain criteria like computational effort (in PoW) or staked tokens (in PoS).
On the other hand, the ordering of transactions within a block typically follows a different set of principles. In many blockchains, especially Ethereum, this ordering is influenced by transaction fees (gas fees). Miners or validators choose which transactions to include in a block based on the fees attached to them, often prioritizing higher-fee transactions for quicker inclusion.
The crux of the problem lies in the fact that these two mechanisms – block sequencing and transaction ordering – operate independently of each other and are guided by different incentives and principles. This disconnection creates a loophole that can be exploited.
Miners or Validators, who are responsible for adding new blocks to the chain, can manipulate the order of transactions within a block to maximize their profits. For example, by engaging in practices like frontrunning, they can place their transactions in a way that benefits from the knowledge of pending transactions in the mempool. This manipulation is made possible because the transaction ordering mechanism (based on fees) is not aligned with the block sequencing mechanism (based on consensus rules).
In an ideal blockchain operation, both block creation and transaction ordering should work towards the same goal – maintaining the integrity and security of the blockchain. However, when transaction ordering is influenced by miner/validator incentives (like maximizing fee revenue), it can conflict with the broader goals of the consensus mechanism, which is focused on securing the network and maintaining a decentralized and fair ledger.
The dual methods seem sensible in their decoupling abstractly but integrate poorly in practice to enable secure sequencing. Instead,
the transaction ordering via fees remains swayed by miner incentives to game pending queues, while
block ordering relies on immutable rules to erase such tempering latitude.
Further, based on how the manipulation occurs across block boundaries, MEV techniques can be categorized as either atomic MEV or non-atomic MEV. Analyzing this distinction provides insights into the different vectors for extraction.
Atomic MEV
Atomic MEV refers to value extraction techniques applied within a single block production by the miner or block creator. These leverage the ability to reorder transactions within one block to engineer profitable outcomes.
Typical examples of atomic MEV include:
Sandwich attacks – Observing a large pending trade, miners front-run the transaction with their own acquisition trade to benefit from the price impact of subsequent large order. The adversarial and victim trades are sequenced in an isolated single block production to guarantee profit capture.
Liquidations – Detecting transactions likely to cause undercollateralized positions, miners delay inclusion deliberately until liquidation conditions are triggered, earning them liquidation penalty revenue. Again the delay and confirmation required happens atomically within one block.
DEX arbitrage – Searchers spot arbitrage opportunities across decentralized exchanges (DEXs) and sequence trades competitively within their privately produced block to capitalize on price discrepancies ahead of any user transactions indicating the opportunity.
The common theme is that atomic MEV techniques do not depend on any changes to subsequent blocks for profits or outcomes. The adversarial transactions are all sequenced within one block production sequence alongside target transactions. This makes the strategy local to one block without peering across multiple blocks for completion.
The key benefit of atomic MEV is simplicity. By containing the attack vector to intra-block reordering, atomic MEV is conceptually and operationally easier to implement for miners than non-atomic approaches. Atomicity guarantees winner takes all profit for the miner through the isolated sequence manipulation.
Metrics to quantify prevalence of atomic MEV include examining total transaction counts and volume for arbitrage or liquidations. Additionally, priority gas auctions can indicate likelihood of sandwich attacks or adversarial sequencings via bribes. Correlating anomalous trading spikes with timestamps of privately produced blocks is also used.
Non-Atomic MEV
In contrast to atomic MEV, non-atomic MEV refers to profit-focused block reorganization techniques that span multiple blocks for completion. This requires deliberate coordination across transactions in separate block productions.
Common examples of non-atomic MEV include:
CEX-DEX arbitrage – Searchers observe pricing divergence across centralized and decentralized exchanges and deliberately delay user transactions to capitalize on lag for higher profiteering. Needs spanning blocks for arbitrage confirmation.
Liquidations – identifying transactions likely to get liquidated if confirmation is intentionally delayed, miners strategically stall inclusion over a few blocks to eventually liquidate and earn revenue.
Prediction manipulation – pending transactions around event outcomes like prediction markets see strategic delays to influence resolutions due to late reveals.
The key aspect of non-atomic MEV is that the sequence manipulation cannot be contained only intra-block, and profits cannot be guaranteed in one single block production. Deliberate re-ordering requires peering across multiple blocks for the final outcome.
For example, delaying trades to eventually liquidate assets depends on the intermediate wait allowing external price changes to cause undercollateralization. This necessitates intentionally stalling inclusion over several blocks - an effect not achievable purely intra-block.
Analyzing volume flows, priority gas payments and capital flows across CEX and DEX can quantify non-atomic MEV. The multi-block span and intentional peering across block productions differentiate it from isolated atomic MEV vectors.
In essence, while atomic MEV simplifies arbitrage to intra-block, non-atomic MEV relies on the miner strategically organizing a cross-block sequence of transactions to manufacture favorable circumstances. This increases complexity but diversifies extraction vectors.
Hybrid MEV
Types As MEV practices continue evolving, hybrid categories are also emerging that blend both cross-block and intra-block reordering for maximally profitable outcomes. For example, front-running a DEX price impact while also delaying a liquidation from the same block shows properties of atomic and non-atomic MEV simultaneously.
Likewise sandwich attacks may originate non-atomically due to transaction delays but culminate atomically within the block that finally sequences both legs for completion. Analyzing both atomic and non-atomic lenses is thus complementary.
Classifying MEV techniques based on atomic versus non-atomic properties provides insights into the manipulation vectors miners utilize.
Atomic remains simpler in profit realization within the same block while non-atomic uses more elaborate reordering across blocks.
Quantifying both forms through data like volume flows or gas prices enables gauging the scale of ecosystem extraction - an area warranting more transparency to restore fairness.
Understanding the cross-block versus intra-block distinction helps map the continuum of MEV behaviors currently skewing decentralization promises.
(In-Action EXAMPLE) Sandwich Attack
A sandwich attack occurs when the attacker places a transaction before and after the victim's transaction to profit from the price movement caused by the victim's transaction.
Overview:
This is executing a swap of WETH to swETH (wrapped Synthetic ETH) on the DeFI platform Composable Finance.
It involves the caller (0x1264f83...) initiating the swap through the Vault contract.
A sandwich attack occurs when when the attacker places a transaction before and after the victim's transaction to profit from the price movement caused by the victim's transaction.
The caller address 0x1264f83b093abbf840ea80a361988d19c7f5a686 initiates the attack by interacting with the Vault contract to swap WETH for swETH.
Victim initiates swap transaction: The victim decides to swap some WETH for swETH using the Composable Finance protocol and submits their transaction. This gets propagated and ends up pending in the mempool.
Attacker sniffs out transaction: The attacker is running an MEV bot that actively monitors pending transactions across several DeFi protocols. It detects the victim's transaction and the opportunity for a sandwich attack.
Attacker frontruns: Before the victim's transaction gets included in a block, the attacker quickly composes and submits a transaction to manipulate the WETH/swETH price and make it less favorable for the victim. This is submitted with a high gas price so miners pick it up first.
Victim's transaction gets sandwiched: The victim's original swap transaction gets included by the miner in the next block. The earlier price move by the attacker means the victim receives less swETH than expected.
Attacker backruns: After the victim's transaction, the attacker executes another transaction to profit from the price impact in the opposite direction. Again this is submitted fast with high fees to be included shortly after.
Attacker profits: When all is settled, the attacker has earned a profit in swETH through their manipulation, while the victim paid more slippage and fees on their swap.
The caller's swap transaction is "sandwiched" between other transactions by the attacker to manipulate pricing and drain profits. The key is coordinating transaction ordering and asset transfers.
MEV Solutions
1. Proposer-Builder Separation (PBS)
The core idea of PBS is to split the roles of block creation into two distinct functions:
proposing blocks and
building blocks.
This separation is designed to mitigate some of the exploitative practices that can occur in the block creation process due to MEV.
Let's dive into the details of PBS, its mechanism, and its implementation in blockchain systems.
In traditional blockchain systems, such as Ethereum, the same entity (usually a miner or validator) is responsible for both selecting transactions from the mempool (the collection of all pending transactions) and compiling them into a block. This entity then proposes this block to be added to the blockchain. In this traditional setup, the entity creating the block can potentially exploit their position to extract additional value (MEV). This can be done by
manipulating the order of transactions,
censoring certain transactions, or
through practices like frontrunning, where the entity places their transactions ahead of others for profit.
The Mechanism of PBS
PBS fundamentally changes the block creation process by dividing the responsibilities between two parties: proposers and builders.
Proposers: They are responsible for proposing new blocks to the blockchain. Their role is to maintain the blockchain's integrity and ensure the continued addition of new blocks.
Builders: They are tasked with compiling and arranging transactions within a block. Builders select transactions from the mempool and decide their order in the block.
Imagine Ethereum is like a big puzzle game where each piece of the puzzle is a transaction (like sending or receiving money). Before, there was only one type of player who both found the puzzle pieces and put them in the right place. Now, with Proposer-Builder Separation, there are two types of players:
one who finds the pieces (Builder) and
another who decides where to put them (Proposer).
This makes the game more fair and less likely for someone to cheat.
In the PBS framework, builders create blocks and then send these blocks to proposers. The proposers, in turn, have the sole responsibility of adding these blocks to the blockchain. Importantly, proposers do not have control over the specific contents of the blocks.
Implementing PBS in a blockchain like Ethereum requires significant protocol changes. It involves creating a system where builders can reliably and securely send block proposals to proposers. PBS implementation often involves a bidding process where builders submit their blocks along with a bid (usually a part of the MEV they can extract). The proposer then selects the block that offers the best bid.
This is how it works in a very simplified way:
Step 1: Setting the Stage for Block Creation
Ethereum 2.0 operates under a PoS consensus mechanism.
Validators are the entities responsible for maintaining the network, similar to miners in Proof of Work (PoW) systems.
Step 2: Introduction of Builders
In the traditional model, validators are responsible for both constructing blocks (by selecting and ordering transactions) and proposing these blocks to be added to the blockchain.
With PBS, a new role is introduced: builders. These entities are specialized in compiling and constructing blocks from pending transactions in the mempool.
Step 3: Builders Compile Blocks
Builders independently gather transactions from the mempool. They consider various factors like transaction fees, potential MEV opportunities, and network rules to compile a block that maximizes value.
Once a block is compiled, the builder creates a block proposal, which includes the block itself and a bid (or fee) that they’re willing to pay to the validator for proposing their block.
Step 4: Proposals are Sent to Validators
Builders send their compiled block proposals to validators. This is usually done through a secure relay network or marketplace where multiple builders can submit their proposals.
Validators receive these proposals and can review them to decide which block to propose.
Step 5: Validators Select and Propose a Block
Validators select a block based on the bids and the quality of the block (ensuring it adheres to network rules and includes valid transactions).
After selection, the validator proposes the chosen block to the blockchain network. This proposal is essentially suggesting to other network participants that this block should be the next one added to the blockchain.
Step 6: Network Validation and Addition of the Block
Other network participants (validators and nodes) validate the proposed block. They check if the block follows the consensus rules and contains valid transactions.
Upon successful validation, the block is added to the blockchain.
Step 7: Payment and Rewards
The builder of the block pays the agreed bid or fee to the validator who proposed their block. This payment is often taken from the block rewards and transaction fees associated with the block.
The validator also receives their portion of the block rewards for their role in maintaining the blockchain network.
How PBS Mitigates Certain Forms of MEV
Reducing the Power of Individual Entities: By separating the roles of proposing and building blocks, PBS reduces the ability of any single entity to manipulate transaction order for their gain. This decentralization of power is key to mitigating MEV.
Fostering Competition Among Builders: Since multiple builders compete to have their blocks chosen by proposers, there is less opportunity for any single builder to consistently manipulate transaction order. This competition can lead to more fair and efficient transaction inclusion.
Limiting Information Asymmetry: In the traditional model, the same entity that sees the transactions in the mempool is also responsible for block creation, leading to potential exploitation. PBS limits this by dividing the responsibilities, thus reducing the chance for information asymmetry to be exploited for MEV.
There has also been a proposal to enshrine PBS:
Arguments for ePBS:
Relays are centralized and oppose Ethereum's values of decentralization, censorship resistance, and trustlessness.
Out-of-protocol solutions like mev-boost are brittle, as shown by recent exploits and bugs.
Relays are expensive to operate as public goods without a clear funding model.
But we will not dive deep into it at the moment as enshrining anything onto the main chain is a complicated discussion, which we discussed here in detail: Just enough and not too much.
2. Protocol-Enforced Proposer Commitments (PEPC)
PEPC is designed to enhance the integrity and efficiency of the block production process by creating a more structured and enforceable framework for the interactions between proposers (validators) and builders (those who compile transactions into blocks).
The Basics of PEPC
PEPC is predicated on the idea of creating a more secure and enforceable system for block proposal and construction in blockchain networks. It seeks to address the limitations of current Proposer-Builder Separation (PBS) models by ensuring that commitments made by proposers to builders are enforceable within the blockchain protocol itself.
In a typical blockchain network like Ethereum, validators (or proposers) are responsible for proposing new blocks to be added to the chain, while builders are tasked with compiling and arranging transactions within these blocks. PEPC aims to regulate the interactions between these two parties more effectively.
Under PEPC, validators make specific commitments to builders about the block's construction. These commitments are enforced by the blockchain protocol, meaning that if a validator fails to honor their commitment, they can be penalized. This enforcement mechanism is designed to enhance trust and reliability in the block production process.
PEPC essentially introduces a contractual framework within the protocol. Validators enter into contracts with builders for the delivery of block content (or other agreed-upon services), and these contracts are honored in an all-or-nothing manner:
either the contract is fully executed with delivery and payment, or
it fails entirely.
How PEPC Enforces Commitments
In PEPC, proposers and builders enter into contractual agreements that are enforced by the blockchain protocol. These agreements specify the terms under which builders compile blocks and proposers subsequently propose them. The commitments made in these agreements are enforced at the protocol level. This means that any deviation from the agreed-upon terms can be detected and penalized by the blockchain system itself, ensuring that both parties adhere to their commitments.
The PEPC system includes mechanisms for penalizing proposers or builders who fail to honor their commitments. These penalties serve as a deterrent against untrustworthy behavior and ensure that both parties have strong incentives to comply with their agreements.
Operational Mechanism of PEPC
PEPC requires integration at a fundamental level within the blockchain protocol. This integration involves modifying the blockchain’s consensus rules to recognize and enforce the commitments made between proposers and builders.
When proposers and builders enter into an agreement, this agreement is recorded on the blockchain. The protocol includes mechanisms to verify whether the actions of proposers and builders are in line with their recorded commitments.
The enforcement of commitments occurs in real-time as blocks are being proposed and added to the blockchain. This immediate enforcement ensures that any violations are swiftly detected and dealt with, maintaining the integrity of the block creation process.
This example is illustrative and assumes the integration of PEPC into a blockchain's protocol.
Step 1: Initialization of the Block Creation Process
In a blockchain network using PBS, the process begins with numerous builders independently monitoring the mempool (a collection of all pending transactions) to compile potential blocks.
Each builder evaluates transactions based on fees, potential MEV opportunities, and other relevant criteria.
Step 2: Entering into PEPC Agreements
A builder, having compiled a block, enters into a PEPC agreement with a proposer. This agreement specifies the terms under which the block will be proposed, including any fees or rewards to be paid to the proposer.
The agreement details are recorded on the blockchain, ensuring that the terms are transparent and enforceable by the network's protocol.
Step 3: Submission of Block Proposals
Builders submit their compiled blocks along with the PEPC agreements to the proposers. These submissions are done through a secure and verifiable mechanism, ensuring the integrity of the process.
Each block proposal is accompanied by a bid or fee offer, which represents the builder's payment to the proposer for block proposal services.
Step 4: Selection of Blocks by Proposers
Proposers receive multiple block proposals from different builders. They review these proposals, evaluating them based on the associated bids, the profitability of the blocks, and their adherence to the network's rules.
A proposer selects a block for proposal to the blockchain. The selection is based not only on the financial bid but also on the compliance of the block with the PEPC agreement.
Step 5: Proposal of the Selected Block
The selected block, along with its PEPC agreement, is proposed by the proposer to the blockchain network. This proposal is effectively a suggestion to other network participants (nodes and validators) that this block should be the next to be added to the blockchain.
Step 6: Network Validation
Other participants in the network validate the proposed block. This validation process involves checking the block's compliance with the blockchain's consensus rules and the terms of the PEPC agreement.
The blockchain protocol plays a crucial role in ensuring that the proposer has adhered to the PEPC agreement. Any deviations or breaches are flagged and can lead to penalties as dictated by the protocol.
Step 7: Finalization and Reward Distribution
Upon successful validation, the block is finalized and added to the blockchain.
The builder pays the agreed-upon fee to the proposer as per the PEPC agreement. This payment is often facilitated by the blockchain protocol, ensuring trustless and automatic execution of the agreement's terms.
Both the proposer and the builder receive their respective rewards and fees, as determined by the block's transaction fees and the blockchain's reward mechanism.
In this hypothetical example, PEPC functions as a protocol-level enforcement mechanism that ensures the integrity and reliability of the PBS process. By making proposer-builder agreements transparent, enforceable, and part of the blockchain's operational protocol, PEPC significantly reduces the potential for exploitative practices and enhances the overall fairness and efficiency of the block creation process.
To illustrate another example of how PEPC works, let us consider a simple example of a full block auction.
Suppose Rex is the proposer for slot n, and she wants to sell her block space to the highest bidder. He can use PEPC to make a credible commitment to do so, as follows:
Rex broadcasts a message to the network, announcing that she is conducting a full block auction for slot “N”. he also specifies a deadline for receiving bids, and a characteristic function that evaluates whether a block satisfies her commitment.
Ben and Adam are interested in bidding for Rex’s block space. They send their bids to Rex, along with a proof of funds and a signature.
Rex collects all the bids he receives before the deadline, and selects the highest one. Suppose Ben is the winner, and he bid 10 ETH for the block space. Rex sends a message to Ben, confirming his bid and providing a signature.
Ben constructs a block that contains his transactions, and pays Rex 10 ETH in the coinbase transaction. He also includes Rex’s signature in the block header, as a proof of her commitment.
Ben broadcasts the block to the network, and hopes that it will be included in the canonical chain.
The network validates the block, and checks whether it satisfies Rex’s commitment. This is done by applying the characteristic function to the block, and verifying Rex’s signature. If the block passes the validation, it is accepted as a valid block for slot “N”. Otherwise, it is rejected as an invalid block.
Again, this is a simplified example of how PEPC works in action. There are many details and challenges that need to be addressed, such as:
How to design the characteristic function, and how to ensure that it is computable and verifiable by the network.
How to prevent or mitigate attacks, such as censorship, front-running, collusion, or denial-of-service.
How to incentivize proposers and bidders to participate in PEPC, and how to balance the trade-offs between efficiency and fairness.
How to integrate PEPC with other features of the Ethereum protocol, such as EIP-1559, ePBS, or sharding.
These examples give us a gist of what to expect and what to build upon.
Strengthening PBS and Mitigating MEV
Enhancing Trust in PBS: By enforcing the commitments made between proposers and builders, PEPC strengthens the overall PBS framework. It ensures that the separation of duties in PBS is not just theoretical but is backed by enforceable rules that all parties must follow.
Mitigating MEV: One of the key objectives of PBS is to mitigate MEV by decentralizing the block creation process. PEPC contributes to this goal by ensuring that the process of assembling and proposing blocks is governed by transparent and enforceable rules, reducing the opportunity for manipulative practices like frontrunning or transaction censorship.
Promoting Fairness and Transparency: The enforcement of commitments in PEPC promotes fairness and transparency in the block creation process. It ensures that builders can trust proposers to honor their agreements, and vice versa, leading to a more equitable blockchain ecosystem.
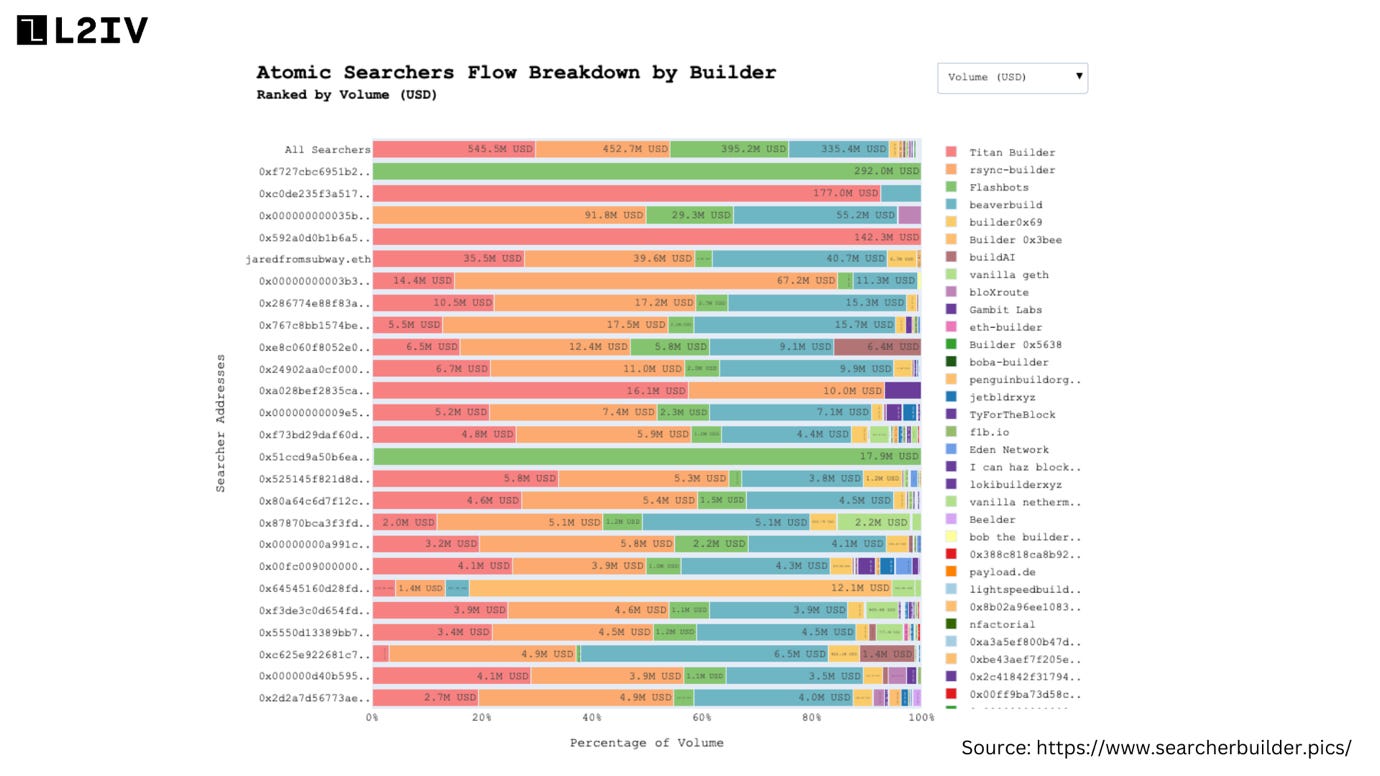
3. Single Unifying Auction for Value Expression (SUAVE)
SUAVE is an independent decentralized network that can serve as a shared mempool and block builder for multiple blockchain domains. The goal is to combat miner/validator extractable value (MEV) centralization risks by providing an open permissionless platform for transaction sequencing and execution.
The core philosophy behind SUAVE stems from the viewpoint that blockchain transaction sequencing and ordering comprises an isolated horizontal layer that can be unbundled as an interoperable service to prevent the centralization risks introduced by unchecked miner/validator extractible value (MEV). By providing credible neutrality, service integrity can benefit all participating chains.
The Premise and Necessity of SUAVE
Flashbots has been working on solutions to address MEV issues, such as MEV-Geth. MEV-Geth is a modified version of the Ethereum client that enables miners to interact with MEV bundles. These bundles are collections of transactions curated by searchers (agents identifying profitable MEV opportunities) for miners to include in blocks.
However, MEV-Geth is not enough to solve the long-term challenges of MEV, such as exclusive order flow and cross-domain MEV.
Exclusive order flow: A key limitation of MEV-Geth is its inability to fully address exclusive order flow, where certain searchers gain privileged access to transactions, leading to an uneven playing field and potential exploitation of user transactions for MEV.
Cross-domain MEV: Another challenge is cross-domain MEV, which involves MEV opportunities that span across multiple blockchains, necessitating complex coordination among validators from different networks.
This is where SUAVE comes in.
SUAVE's Role as Mempool and Block Builder: SUAVE emerges as a distinct blockchain network designed to function as both a Mempool and a Block Builder for all EVM (Ethereum Virtual Machine)-compatible blockchains. This approach aims to unbundle these roles from existing blockchain infrastructures.
Decentralization of Mempool and Block Building: By operating as a separate entity, SUAVE seeks to decentralize the process of transaction selection and block construction. This decentralization can mitigate the risks associated with exclusive order flow by creating a more open and equitable environment for transaction processing.
SUAVE is structured to facilitate cross-chain coordination, addressing the challenge of cross-domain MEV. It allows for a unified approach to transaction ordering and block building across different blockchain networks, enhancing efficiency and reducing the likelihood of exploitative practices. SUAVE's specialization in being a mempool and block builder enables it to focus solely on these functions, potentially executing them more efficiently than traditional blockchain networks. Its decentralized nature aligns with blockchain's core principle of distributed power and control.
SUAVE in the Blockchain Stack
Independent Network: SUAVE is conceptualized as an independent network that acts as a plug-and-play mempool and decentralized block builder for any blockchain. While it's a new blockchain, it's not a general-purpose smart contract platform but rather focuses on unbundling the mempool and block builder role from existing chains.
Multi-Chain Application: Unlike systems designed for a single blockchain, SUAVE is meant to serve as the mempool and block builder for all blockchains, leveraging its neutrality to aggregate preferences and strategies in a single place.
Benefits of SUAVE
For Blockchains: It provides decentralized sequencing and network resilience.
For Validators: It maximizes revenue potential from their block space.
For Builders/Searchers: It offers open access to user transactions and enables complex, cross-chain coordination.
For Users: It ensures transaction privacy, optimal execution, and minimized fees.
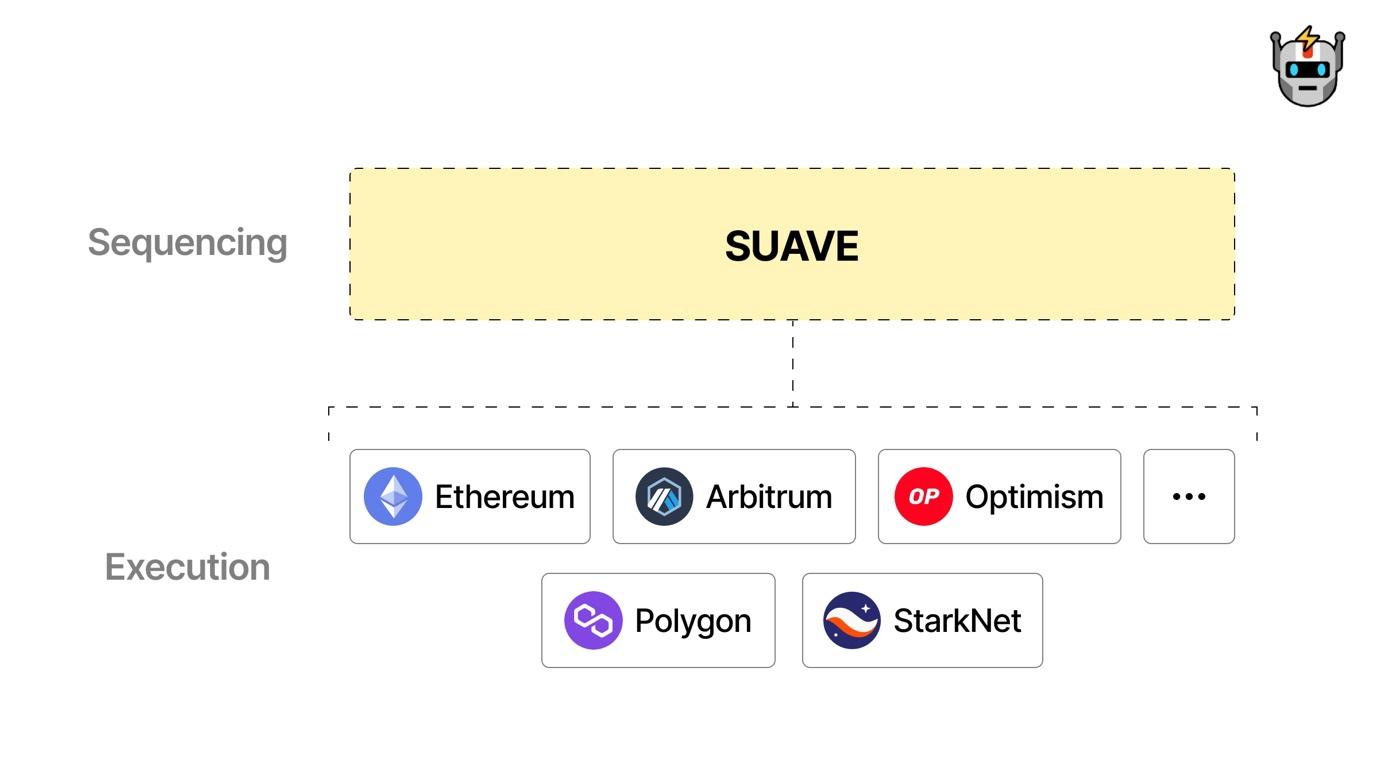
SUAVE Architecture
Universal Preference Environment: A specialized chain and mempool for preference expression and settlement, aggregating user and searcher preferences across participating chains.
Users initiate by submitting transaction preferences that encode desired pricing parameters, assets, targets, and complex multi-step scripts potentially spanning domains. This acts as the universal preference environment.
The preference environment allowing customizable conditional transaction logic poses design questions around striking the right balance between expressiveness and simplicity. Overly complex user-specified preferences could become unexecutable. Methodical expansions of preference vocabulary could promote organic adoption.
Optimal Execution Market: A network where executors compete to provide the best execution for user preferences, addressing a wide range of user needs across various domains.
The execution market comprises professional executor nodes who intake user preferences, rapidly explore implication vectors across chains to optimize routing, pricing and packaging tactics to best satisfy preference guidance. Machine learning, data oracles, competitive auctions amongst executors promote maximal fulfillment.
The execution market redistributing MEV profits to preference originators appears an advance over status quo. However, equitable splits between users, searchers, executors and builders should involve transparent governance based on role value addition, not just monopolistic middlemen.
Decentralized Block Building: A network fostering collaboration among block builders to access encrypted user preferences and compile them into blocks.
Having applied intelligence to unpack opportunities in submitted preferences across domains, optimized bundles get passed to the decentralized block building role.
This enables open participation where builder nodes sequence transactions for target chains - collaborating to construct blocks that maximize utility for submissions based on the previously applied preference fulfillment strategies.
The decentralized block building ecosystem poses chicken-and-egg adoption challenges. A hybrid bridge allowing legacy block builders to interface during gradual onboarding could offset risks of fragmentation. Trusted hardware enclaves could assist managing privacy-preserving order flow sharing across incumbent and newer builders.
SUAVE introduces a Unified Auction Mechanism
Under SUAVE, Some examples of value expressions are:
User transactions: These are the normal transactions that users send to the network, such as transfers, swaps, or smart contract interactions. Users can express their value by specifying the maximum fee they are willing to pay for their transactions, and the minimum execution guarantee they require.
MEV bundles: These are the transactions that searchers send to the network, which exploit profitable MEV opportunities, such as arbitrage, liquidation, or sandwiching. Searchers can express their value by specifying the minimum fee they are willing to pay for their MEV bundles, and the maximum execution risk they can tolerate.
Block proposals: These are the blocks that builders send to the network, which contain a selection and ordering of transactions and MEV bundles. Builders can express their value by specifying the minimum reward they expect for their block proposals, and the maximum deviation they can accept from their preferred block.
SUAVE’s unified auction mechanism allows these different types of value expressions to compete and cooperate with each other, creating a more efficient and fair market for transaction processing and MEV extraction.
This is how it is structured:
Auction-Based Transaction Ordering:
SUAVE proposes a marketplace where transactions are ordered based on a unified auction system. Instead of the traditional first-come, first-served or gas-price-based ordering, transactions are prioritized based on bids placed in an auction setting.
This auction system aims to maximize the efficiency of block space utilization by aligning incentives between
users (who want their transactions processed) and
validators/builders (who want to maximize block rewards).
Cross-Chain Coordination:
Unique to SUAVE is its cross-chain approach. It doesn’t just cater to a single blockchain but aims to serve as a sequencing layer for multiple blockchains.
This cross-domain integration means builders and validators from different blockchains can participate in a single, unified auction market. This approach potentially increases efficiency and optimizes MEV extraction across the blockchain ecosystem.
Transparent and Open Participation:
The SUAVE platform is envisioned as open and permissionless, allowing any participant to join the auction for block space. This transparency could lead to more competitive bidding and fairer transaction processing prices.
By democratizing access to block space auctions, SUAVE can potentially reduce the advantage of centralized entities that currently dominate the transaction ordering process.
SUAVE in Action
Let’s illustrate SUAVE's role as a decentralized mempool and block builder network, particularly for EVM-compatible blockchains.
Here is a detailed step-by-step explanation of how SUAVE (Single Unifying Auction for Value Expression) proposes to operate:
This scenario will illustrate SUAVE's role as a decentralized mempool and block builder network, particularly for EVM-compatible blockchains.
Step 1: Transaction Submission to SUAVE
Users Submit Transactions: Users from various EVM-compatible blockchains submit their transactions to the SUAVE network. These transactions could include simple transfers, complex smart contract interactions, or cross-chain operations.
Privacy and MEV Protection: Transactions in SUAVE are handled with pre-confirmation privacy, ensuring that users' intentions are not exposed to MEV searchers prematurely.
Step 2: Aggregation of Preferences in SUAVE
Preference Expression: SUAVE aggregates these transactions, treating them as expressions of user preferences. These preferences are not just specific instructions but can also include conditions or desired outcomes.
Optimizing Execution Paths: Executors in SUAVE analyze these preferences to determine optimal execution paths. This could involve batching similar transactions or identifying cross-chain opportunities for MEV redistribution back to users.
Step 3: Auction for Transaction Processing
Unified Auction Mechanism: Builders (block creators) across various blockchains participate in SUAVE’s unified auction to bid for the right to process these transactions. The auction is designed to maximize efficiency and reward distribution.
Bidding by Builders: Builders place bids based on the perceived value of the transaction sets, including potential MEV. The highest bidders win the right to process the transactions.
Step 4: Block Construction Across Chains
Cross-Chain Coordination: Winning builders construct blocks for their respective blockchains. Given SUAVE’s cross-chain nature, this process is coordinated across different networks, optimizing for global MEV distribution and network efficiency.
Decentralized Block Building: SUAVE facilitates a decentralized approach to block building, where multiple builders can collaboratively work on constructing blocks.
Step 5: Execution and Settlement
Execution of Transactions: Executors in the SUAVE network ensure that transactions are executed as per the users’ preferences. This could involve complex sequences of events across multiple blockchains.
Settlement: Once executed, the transactions are settled on their respective blockchains. This process includes the transfer of assets, execution of smart contracts, or any other blockchain-specific operations.
Step 6: Reward Distribution
Payments and Rewards: Users pay transaction fees as per the terms of the auction. These fees, along with any redistributed MEV, are shared among the builders, validators, and, where applicable, the users themselves.
Incentive Alignment: This mechanism ensures that all parties involved are incentivized to act in the best interests of the network and the users, aligning rewards with efficient and fair transaction processing.
In this hypothetical example, SUAVE operates as an advanced, decentralized platform that unifies transaction processing across multiple blockchains. It optimizes for user privacy, efficient MEV redistribution, and cross-chain coordination, representing a significant step towards a more interconnected and user-centric blockchain ecosystem.
To illustrate how SUAVE works in action, let us consider a simple example of a user transaction on Ethereum.
Suppose Alexia wants to swap some ETH for DAI on Uniswap, a decentralized exchange. She can use SUAVE to execute her transaction as follows:
Alexia submits her transaction to SUAVE, instead of directly to Ethereum. She specifies the maximum fee she is willing to pay for her transaction, and the minimum execution guarantee she requires. For example, she may set a fee of 0.01 ETH, and a guarantee of 95%, meaning that she expects her transaction to be executed with at least 95% probability.
SUAVE receives Alexia’s transaction, and assigns it a unique identifier. SUAVE also broadcasts Alexia’s transaction to the network, making it visible to other participants, such as searchers and builders.
Searchers monitor the network and look for profitable MEV opportunities, such as arbitrage, liquidation, or sandwiching. They may find that Alexia’s transaction can be exploited for MEV, by inserting their own transactions before or after Alexia’s transaction, to manipulate the price of ETH and DAI on Uniswap.
Searchers bundle their transactions with Alexia’s transaction, and send them to SUAVE as MEV bundles, along with a bid or fee offer. For example, a searcher may offer 0.005 ETH to SUAVE for including their MEV bundle, which contains Alexia’s transaction and two other transactions that sandwich it.
SUAVE collects all the MEV bundles that contain Alexia’s transaction, and evaluates them based on the bids, the profitability, and the compliance with Alexia’s execution guarantee. SUAVE selects the best MEV bundle for Alexia’s transaction, and assigns it to a builder.
Builders collect transactions and MEV bundles from SUAVE, and construct blocks for different blockchains. A builder who receives Alexia’s transaction and the selected MEV bundle constructs a block for Ethereum, and sends it to SUAVE as a block proposal, along with a reward offer. For example, a builder may request 0.01 ETH from SUAVE for proposing their block, which contains Alexia’s transaction, the selected MEV bundle, and other transactions.
SUAVE collects all the block proposals for Ethereum, and evaluates them based on the rewards, the profitability, and the compliance with the network’s rules. SUAVE selects the best block proposal for Ethereum, and assigns it to a validator.
Validators receive blocks from SUAVE, and propose them to their target blockchain. A validator who receives the selected block for Ethereum proposes it to the Ethereum network, and hopes that it will be included in the canonical chain.
The Ethereum network validates the proposed block, and checks whether it satisfies the network’s consensus rules. If the block passes the validation, it is accepted as a valid block for Ethereum. Otherwise, it is rejected as an invalid block.
Upon successful validation, the block is finalized and added to the Ethereum blockchain. Alexia’s transaction is executed, and she receives her DAI in exchange for her ETH. The searcher who submitted the selected MEV bundle receives their MEV profit, and pays their bid or fee to SUAVE. The builder who constructed the selected block receives their block reward and transaction fees, and pays their reward offer to SUAVE. The validator who proposed the selected block receives their bid or fee from SUAVE, in addition to the block reward and transaction fees from the Ethereum network.
With the above example, we aim to
Show the modular roles of key players like searchers, builders, and validators and how they interact with SUAVE for different duties.
Illustrate the economic incentives via bids, reward offers that align behaviors.
Depict critical steps of broadcast, bundling, block proposal, validation etc. that enable transparency and execution integrity.
Show end-to-end flow covering submission to settlement represents real-life workflow.
SUAVE’s Complementation of PBS and PEPC
Enhancing PBS:
SUAVE complements PBS by providing a decentralized, auction-based platform where these separated roles can interact more efficiently.
In a PBS environment, builders can use the SUAVE auction to bid for the right to have their blocks proposed, creating a competitive and transparent market for block space.
Strengthening PEPC:
PEPC ensures that the commitments made by proposers to builders are honored and enforced at the protocol level. SUAVE can support PEPC by offering a transparent and accountable platform for these commitments to be made and executed.
The unified auction mechanism in SUAVE can serve as a verifiable and open market where PEPC agreements are executed, ensuring that proposers and builders adhere to their commitments.
Market Efficiency and Transparency:
SUAVE’s auction mechanism introduces market efficiency by allowing transaction ordering to be determined through competitive bidding rather than opaque or potentially manipulative processes.
The transparency of the auction process aligns with the goals of PBS and PEPC to create a more decentralized and fair blockchain ecosystem. It reduces the likelihood of MEV exploitation by making the transaction ordering process more transparent and less susceptible to manipulation.
By isolating the transaction ordering layer as specialized infrastructure, SUAVE also quarantines the MEV revenue potential avoiding contamination of base chain security. Positive competition incentivizes permissionless participation in sequencing by applying market forces and opportunities for efficiency across preference exploration, execution optimization and block construction with user privacy safeguarded throughout the pipeline.
For validators of multiple chains, shared access promotes sustainability and broadens miner incentives.
For users, benefits include preference flexibility, privacy, optimal pricing, and cross-domain capital flows.
4. MEV-Boost
mev-boost was developed by Flashbots in collaboration with the community to mitigate the negative impacts of MEV on the Ethereum network, particularly in the context of Ethereum's transition to PoS.
Key Actors in mev-boost
Relays: These act as intermediaries or auctioneers, connecting proposers (Ethereum PoS validators) to block builders. They play a crucial role in facilitating the fair exchange of block space and transaction sequencing.
Builders: These are sophisticated entities focused on constructing blocks to maximize MEV. They curate transactions from various sources, including users and searchers, aiming to extract maximum value.
Proposers: In Ethereum's PoS context, proposers are validators responsible for proposing blocks to be added to the blockchain.
Process Flow in mev-boost

Block Creation: Builders create a block using transactions from various sources.
Submission to Relay: The constructed block is submitted to a relay.
Validation and Payment Calculation: The relay validates the block's legitimacy and calculates the payment to the proposer.
Blinded Header Transmission: The proposer receives a blinded block header and payment value from the relay.
Evaluation and Signing by Proposer: The proposer evaluates bids received and signs the blinded header associated with the highest payment.
Block Publishing: The signed header is sent back to the relay, which then publishes the block using their local beacon nodes. This process includes distributing rewards to both the builder and proposer.
Reward Distribution: Rewards are distributed through transactions within the block and the block reward mechanism.
MEV-Boost is an implementation of PBS.
mev-boost practically implements proposer-builder separation by unbundling duties to expand participation in transaction ordering and block construction. The mutual custodians introduce trust constraints unlike pure PBS, but coordination efficiencies may offer sustainability.
How mev-boost enables Proposer-Builder Separation:
Decouples block proposing from building: In traditional models, validators both propose and build block contents. mev-boost splits these into separate roles - proposers validate while builders construct block contents.
Proposer outsourcing of duties: mev-boost allows proposers to outsource all block construction responsibilities to specialized external builders who can maximize profitable ordering.
Relays coordinate assignment: Relays act as mutual custodians matching builders to proposers each round based on bids and payments offered. This prevents direct proposer-builder relationships.
Expands ecosystem participation: Opens up access to anyone to fulfill discrete building and validation activities based on capabilities. Reduces centralized control.
Importance of mev-boost
mev-boost addresses the issues arising from MEV, such as transaction reordering, front-running, and other manipulative practices that can negatively impact network fairness and user experience.
By providing a mechanism for all proposers to access MEV opportunities without needing established trust with builders or searchers, mev-boost contributes to the decentralization and democratization of MEV extraction. This is especially important in maintaining the ethos of Ethereum as a decentralized platform.
Relays in mev-boost prevent MEV stealing by proposers and ensure the integrity and fairness of transactions within a block. They also alleviate the burden on proposers by processing numerous block proposals and guaranteeing payment accuracy.
MEV Services & Tools

The roles played by various tools and services in the MEV ecosystem are multifaceted and crucial for addressing the challenges and opportunities presented by MEV in blockchain networks. These roles can be categorized into research and transparency, mitigation and protection, distribution and access democratization, and policy and incentives alignment.
1. Research and Transparency
Organizations like OpenMEV, Flashbots, and Eden Network have been instrumental in conducting comprehensive research to quantify and analyze MEV.
Their work involves assessing the impacts of MEV on the blockchain ecosystem and providing insights into the behaviors surrounding value extraction.
By introducing conceptual models and compiling data, they enhance the overall understanding of MEV.
This research is vital for developing informed strategies to address MEV-related issues and for fostering a transparent environment where the implications of MEV are well-understood by all ecosystem participants.
2. Mitigation and Protection
Tools and services like Flashbots, Eden Network, BloXroute, Manifold Finance, MEV-Blocker, Wallet Boost, and MEV-Share focus on developing technical solutions to mitigate the negative impacts of predatory MEV strategies.
They offer protection against practices such as frontrunning (where miners execute their transactions ahead of user-submitted ones for profit) and censorship (where miners selectively exclude certain transactions).
By implementing these solutions, they aim to safeguard end-users from the more exploitative aspects of MEV, ensuring fairer transaction processing and enhancing the overall security and integrity of the blockchain network.
3. Distribution and Access Democratization
Platforms like Flashbots Auctions, Eden Network’s Priority Gas Auctions (PGAs), and MEV-Boost work towards democratizing access to the transaction ordering process in blockchains.
These tools and services aim to distribute the ability to extract value from transaction ordering more equitably, moving beyond the scenario where only a few dominant miners control this aspect.
They introduce revenue-sharing models and open up opportunities for a broader range of participants to engage in and benefit from the transaction ordering process within the blockchain.
4. Policy and Incentives Alignment
Organizations such as Flashbots also play a crucial role in advocating for changes in the blockchain ecosystem that discourage harmful forms of MEV.
Their focus is on realigning incentives to prioritize security, fairness, and decentralization, moving away from an environment driven primarily by profit-seeking behaviors.
By pushing for policy changes and adjustments in the incentive structures, these groups aim to create a more sustainable and equitable blockchain ecosystem, where MEV is managed in a way that benefits the network and its users.
In the MEV landscape, while some entities actively engage in the extraction of value, a significant number are dedicated to enhancing transparency, protecting users, fostering equitable participation in transaction sequencing, and advocating for policy changes that manage MEV constructively. The diverse range of tools and services in this space reflects a comprehensive approach, covering both offensive strategies to extract MEV and defensive strategies to protect against its negative impacts. This duality is essential for maintaining a balanced and fair blockchain ecosystem where the benefits of MEV can be harnessed without compromising the network’s integrity or user trust.
Conclusion
MEV, at present, has posed critical economic and architectural challenges in public blockchain networks that necessitate urgent solutions. Unchecked extraction risks compromising incentives around consensus participation, availability guarantees, settlement finality and overall progression liveness.
Users also suffer from predatory outcomes like front-running, censorship or deliberately adversarial transaction reorderings that cause loss in predictable pricing or execution. And the relentless drive towards maximizing extraction revenues produces acute centralization pressure amongst validators, further eroding decentralization promises.
Promising solutions have emerged and are still emerging – both architectural and coordination based. Approaches like Proposer-Builder Separation (PBS), Protocol-Enforced Proposer Commitments (PEPC), and proposed models such as Single Unifying Auction for Value Expression (SUAVE) provide frameworks to bound manipulation risks by partitioning duties and enforcing mutual obligations on-chain.
Additionally, relay networks attempt coordination between miners and external aggregators. However, reliance on proprietary systems clashes with the philosophy of public blockchains.
Truly sustainable mitigation of MEV necessitates reshaping the deeply interconnected planes of transaction scheduling and block versioning. Fundamental retooling that institutes uniform commitment schemes resistant equitably to observable manipulation and binds incentives for users and infrastructures alike appears to be the most principled approach.
However, the community finds itself at this pivotal junction where economic and social forces challenge technical limits.
Find L2IV at l2iterative.com and on Twitter @l2iterative
Author: Arhat Bhagwatkar, Research Analyst, L2IV (@0xArhat)
References
The MEV Supply Chain: a peek into the future of this industry
Cost of MEV: Quantifying Economic (un)Fairness in the Decentralized World - Tarun Chitra
Disclaimer: This content is provided for informational purposes only and should not be relied upon as legal, business, investment, or tax advice. You should consult your own advisors as to those matters. References to any securities or digital assets are for illustrative purposes only, and do not constitute an investment recommendation or offer to provide investment advisory services.